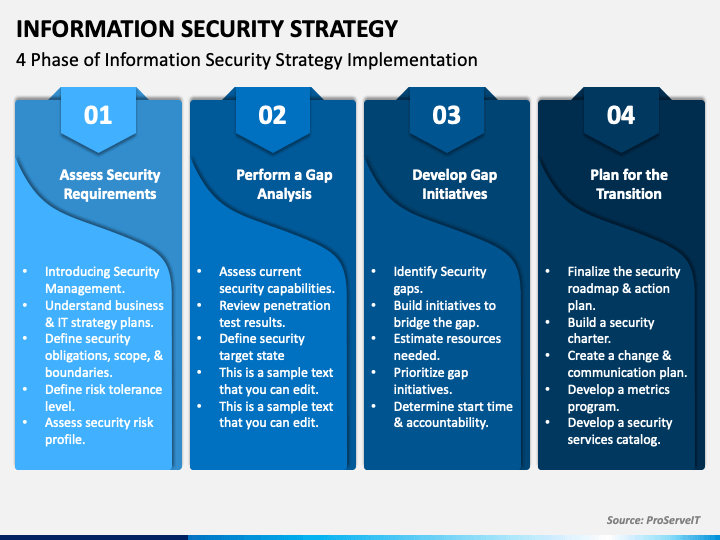
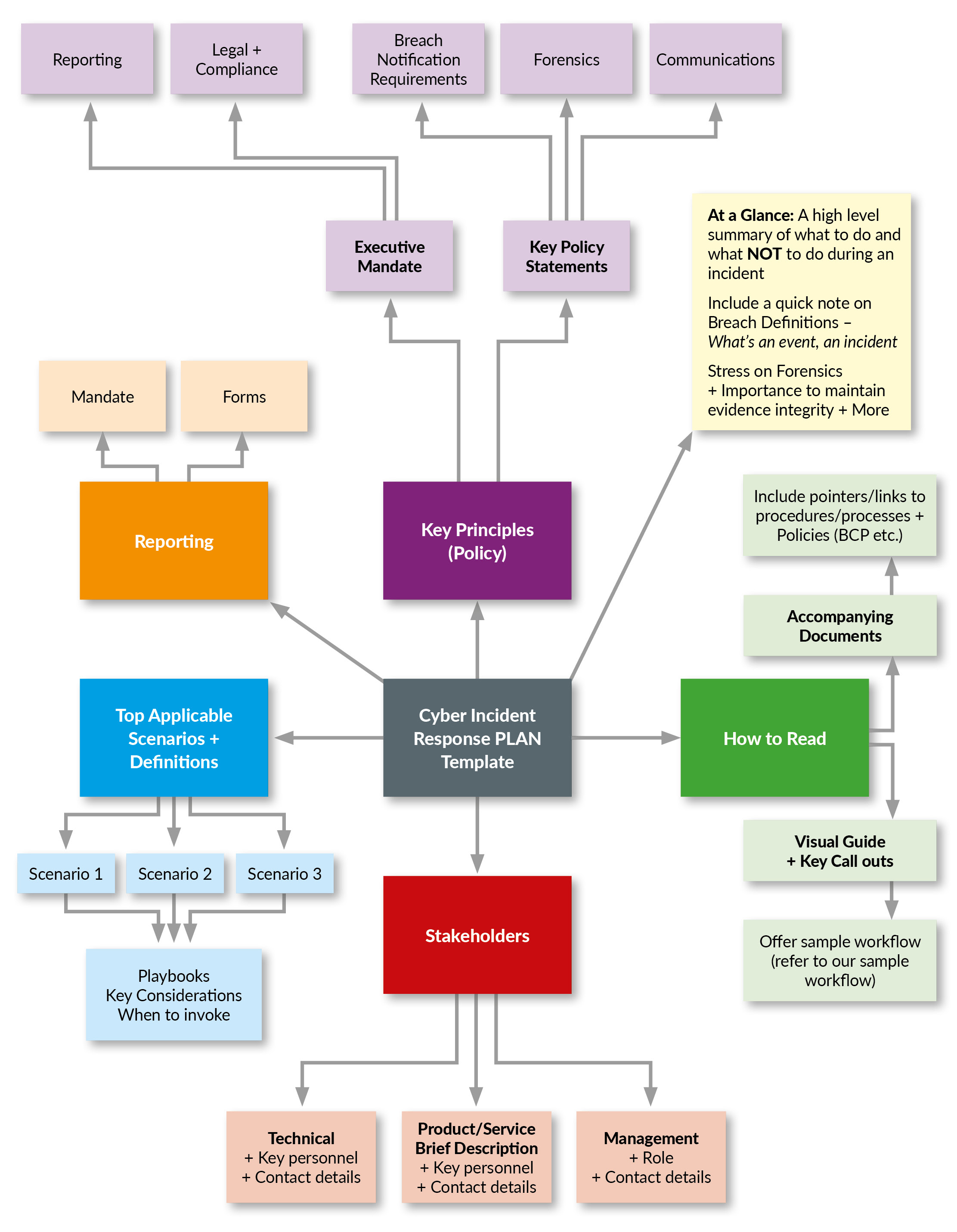
Security Strategy Template
Security Strategy Template - A successful security strategy cannot be developed in isolation. Security and risk management leaders must recognize a range of.
Security and risk management leaders must recognize a range of. A successful security strategy cannot be developed in isolation.
A successful security strategy cannot be developed in isolation. Security and risk management leaders must recognize a range of.
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
A successful security strategy cannot be developed in isolation. Security and risk management leaders must recognize a range of.
Cybersecurity Strategy PowerPoint and Google Slides Template PPT Slides
Security and risk management leaders must recognize a range of. A successful security strategy cannot be developed in isolation.
Cybersecurity Strategy Template
Security and risk management leaders must recognize a range of. A successful security strategy cannot be developed in isolation.
Cybersecurity Strategy Template
A successful security strategy cannot be developed in isolation. Security and risk management leaders must recognize a range of.
Security Plan Templates 15+ Docs, Free Downloads
A successful security strategy cannot be developed in isolation. Security and risk management leaders must recognize a range of.
Cyber Security Implementation Plan Template
Security and risk management leaders must recognize a range of. A successful security strategy cannot be developed in isolation.
FREE 8+ Sample Security Plan Templates in PDF MS Word Google Docs
Security and risk management leaders must recognize a range of. A successful security strategy cannot be developed in isolation.
10+ Security Plan Templates Sample Templates
Security and risk management leaders must recognize a range of. A successful security strategy cannot be developed in isolation.
Information Security Strategy PowerPoint and Google Slides Template
Security and risk management leaders must recognize a range of. A successful security strategy cannot be developed in isolation.
A Successful Security Strategy Cannot Be Developed In Isolation.
Security and risk management leaders must recognize a range of.
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-08.jpg)